Field Frequencies
Community Events
Connecting and empowering IAM through shared events, insights, and collaboration. Sign up to lead the local chapter!
Heading 1
with a request body that specifies how to map the columns of your import file to the associated CRM properties in HubSpot.... In the request JSON, define the import file details, including mapping the spreadsheet's columns to HubSpot data. Your request JSON should include the following fields:... entry for each column.

Modern cloud services rely on agent background services that collect signals, monitor environments, and support intelligent functionality. Here will break down what Azure Agent Services are, how they operate across hybrid and cloud-native environments, and what transparency, security, automation & control really look like. We’ll touch on common scenarios like Azure Monitor, Arc-enabled machines, identity sync with Entra ID, and how agents interact with infrastructure.

Microsoft Identity Manager (MIM) has been holding down the identity fort for years, but it’s showing its age. In this 30-minute episode, will break down what it really takes to move on from MIM, from red flags that suggest you're not ready, to green lights that signal you're set for modernization. It’s a quick, focused take on replacing legacy IAM with scalable, policy-driven identity lifecycle solutions. Whether you're exploring Entra, traditional IGA tools, or something custom, you'll leave with a few talking points to approach with clarity and control.

We’ll cover Entra, attacker visibility, and remediation — including how to leverage Microsoft Graph to map identity relationships and uncover paths for lateral movement and exploitation.

Need the path. Need the plan. Personal favorite topic. A well-designed IAM program ensures smooth (or as smooth as possible) identity governance, secure access management, and a strong foundation for advanced security tools like XSIAM and beyond. The ‘Plan’ doesn’t have to be complicated—but it must be simple, visible, and loud enough to be heard.
Will talk about free blueprints, strategies and more.

B2B CIAM (Customer Identity and Access Management) is crucial for securely managing external client and partner identities, improving user experience, and ensuring regulatory compliance in B2B environments. Join us in exploring B2B CIAM space. We will be discussing:
- What is B2B CIAM
- Business models
- Capabilities expected from a B2B CIAM provider
- Demo

Identity Governance and Access Reviews, weaving together AI, real-time automation, and of course Zero Trust Architecture—connecting every thread in our colony. Addressing challenges and solutions with a nod to ants, spiders,and all of us working together. Q&A, real-world examples, and tech that are both accessible and potentially inspiring.


Featured in this month’s national podcast, we’ll be hosting an unscripted conversation with our guest CISO, diving into topics such as Identity Inventory, reducing the identity ‘Attack Surface’ by securing AD domains and local admin accounts, and the importance of understanding key identity OEM vendors strengths & weaknesses.
Hope to see/hear you there!

Asset management, of course, is not just about devices—identities are at the core. IAM should be treated with intention, not as an afterthought or a cyber insurance checkbox. We aim to foster a culture where IAM responsibilities are clearly defined, communicated, and executed. IAM must be regarded as essential as applications, data, and infrastructure. I’m excited about the yellow brick/rainbow road this approach could pave for the future!

Discussing recent Identity conference, highlights, interesting tech & conversations. The progress of Identity Management to Identity Security.
Collaboration/Bones needed for the ship to operate up and down stream. Similar to the Vikings. See they turned chaos into commerce. But different than the Vikings, will not be destroyed by cannons.

Next chapter event is scheduled for Tuesday, November 7th, from 6PM-9PM and it will take place at Punch Bowl Social in Downtown Sacramento.
Our sponsor and presenter AOHWV will share their experiences and approaches with implementing zero trust architecture with dual identity parameters. They will speak in detail about this topic and useful ways to truly implement.

How to consolidate & securely onboard and manage access to Enterprise AI platforms and Enterprise apps. Talking architecture, just in time provisioning, mapping identity attributes, automation and how to present to the business and end users.
As identity continues to become the new perimeter, attackers will continue to shift tactics and abuse credentials and access paths. Talking here on ITDR the 2nd identity perimeter! How this integrates with SIEM/SOAR platforms for additional intelligence. MFA for all (including legacy application) and what products are offered in this space. See you there!

Cleaning and modernizing AD/AAD structure. The hidden source of access sprawl. How to identify unused or redundant groups, elevate nested group risk, discover un-used contractor or ex employees that still have access.

Join us this time in Texas while we continue to spread the word of Identity + Security. Common themes include conditional access, JML automation, entitlement management and password-less potentials.
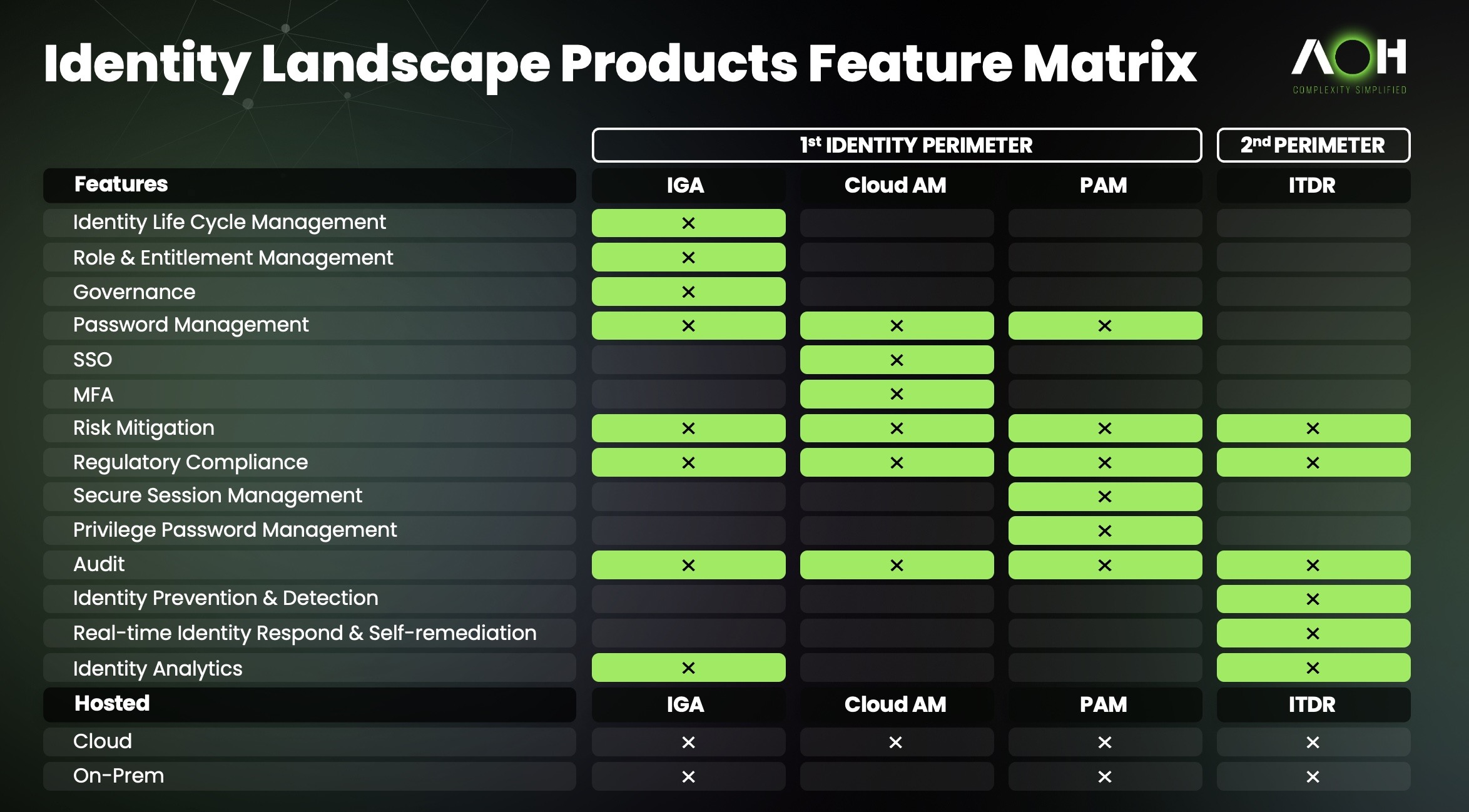

Active Directory has been the backbone of enterprise identity for over two decades but the shift toward hybrid and AAD, Zero Trust models and identity as a service is accelerating its decline. While it will not disappear any time soon, organizations still relying solely on AD for access control, authentication and identity lifecycle management deal with increase complexity and risk. Microsoft focus has shifted to Entra ID (formally Azure AD) showing an increased evolution in how identity will be managed. Should be some good talks.

Wij zijn experts op het gebied van CRM technologie, implementatie en optimalisatie1111
Wij zijn experts op het gebied van CRM technologie, implementatie en optimalisatie1111
Dive into blogs section where our AI experts share their knowledge, practical tips, and industry trends. Stay updated with the latest advancements and explore diverse perspectives on AI applications.

The Identity Landscape and How It Matters
Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book.

The Identity Landscape and How It Matters
Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book.

The Identity Landscape and How It Matters
Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book.

The Identity Landscape and How It Matters
Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book.

The Identity Landscape and How It Matters
Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book.
Recent Publications
Our Latest Blogs
Dive into blogs section where our AI experts share their knowledge, practical tips, and industry trends. Stay updated with the latest advancements and explore diverse perspectives on AI applications.

The Identity Landscape and How It Matters
Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book.

The Identity Landscape and How It Matters
Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book.

The Identity Landscape and How It Matters
Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book.

The Identity Landscape and How It Matters
Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book.

The Identity Landscape and How It Matters
Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book.
Conditional Access Reality Check
Heading 1
with a request body that specifies how to map the columns of your import file to the associated CRM properties in HubSpot.... In the request JSON, define the import file details, including mapping the spreadsheet's columns to HubSpot data. Your request JSON should include the following fields:... entry for each column.
